Equifax isn't the only credit-reporting behemoth with a website redirecting visitors to fake Adobe Flash updates. A security researcher from AV provider Malwarebytes said transunioncentroamerica.com, a TransUnion site serving people in Central America, is also sending visitors to the fraudulent updates and other types of malicious pages.
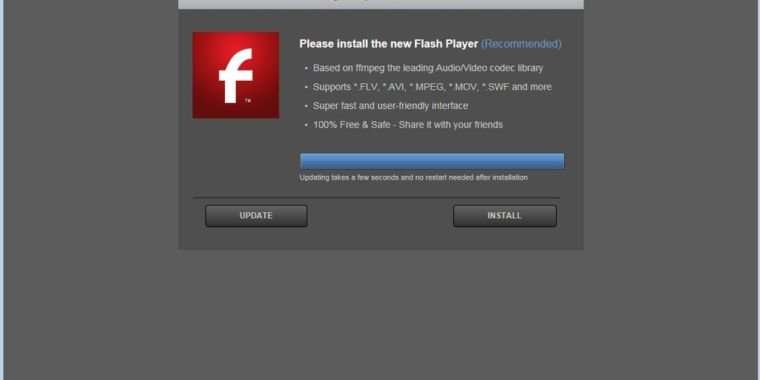
As Ars reported late Wednesday night, a portion of Equifax's website was redirecting visitors to a page that was delivering fraudulent Adobe Flash updates. When clicked, the files infected visitors' computers with adware that was detected by only three of 65 antivirus providers. On Thursday afternoon, Equifax officials said the mishap was the result of a third-party service Equifax was using to collect website-performance data and that the "vendor's code running on an Equifax website was serving malicious content." Equifax initially shut down the affected portion of its site, but the company has since restored it after removing the malicious content.
Now, Malwarebytes security researcher Jérôme Segura says he was able to repeatedly reproduce a similar chain of fraudulent redirects when he pointed his browser to the transunioncentroamerica.com site. On some occasions, the final link in the chain would push a fake Flash update. In other cases, it delivered an exploit kit that tried to infect computers with unpatched browsers or browser plugins. The attack chain remained active at the time this post was going live. Segura published this blog post shortly after this article went live on Ars.
"This is not something users want to have," Segura told Ars.
Three hours after this post went live, a TransUnion spokesman sent an e-mail that said: "TransUnion is aware that our Central America website was temporarily redirecting users to download malicious software. The issue has been fixed and we are scanning our other websites. TransUnion has not identified any unauthorized access to its systems as a result of this issue."
The common thread tying the affected Equifax and TransUnion pages is that both hosted fireclick.js, a JavaScript file that appears to invoke the service serving the malicious content. When called, fireclick.js pulls content from a long chain of pages, starting with those hosted by akamai.com, sitestats.com, and ostats.net. Depending on the visitors' IP address, browsers ultimately wind up visiting pages that deliver a fake survey, a fake Flash update, or an exploit kit.
Segura believes ostats.net is the link in the chain where things turn bad, but he has yet to confirm that. The full chain in one transunioncentroamerica.com redirect looked like this:
The following GIF image captures the redirection sequence in action:
Ostats.net also played a role in the redirects that took place on the affected Equifax Web page. A video taken by independent security analyst Randy Abrams showed it sending him to a series of malicious sites that ultimately lead to the adware lure.
Attempts to reach people who own the domain weren't immediately successful. Ars e-mailed a spokesman at TransUnion to notify him of Segura's finding. Until TransUnion has time to respond, people should remain wary of the company's various Web properties, particularly the one serving Central America.
Equifax on Thursday was quick to say that its systems were never compromised in the attacks. TransUnion said much the same thing. This is an important distinction in some respects because it means that the redirections weren't the result of attackers having access to restricted parts of either company's networks. At the same time, the incidents show that visitors to both sites remain much more vulnerable to malicious content than they should be. What's more, infected visitors aren't likely to take much comfort in that clarification, either.
Updated to add comment from TransUnion.
powersurge on October 14th, 2017 at 17:03 UTC »
Please see my other comments for a guide on how to put credit freezes on at all three agencies through their phone systems. The phone systems avoid all of these companies' efforts to divert you to monitoring plans.
fiatpete on October 14th, 2017 at 16:45 UTC »
I guess they also want an IRS contract ;-)
A_Galio_Main on October 14th, 2017 at 16:35 UTC »
How does this keep happening!?